We help Organizations protect their data
against internal and external data breaches
Prosoft provides Data Security services that help organizations reduce the risk of a data breach and simplify compliance with innovative data security solutions for encryption, key management, data masking, data redaction, privileged user access controls, activity monitoring, and auditing.
Prosoft works closely with its clients to help them comply with data security standards and regulations. We provide a comprehensive approach ranging from architecture design to the implementation of data security solution.

Security requirements for compliance standards such as CISP, HIPAA, and PCI have increasingly emphasized data-at-rest encryption as a last-line of defense against data-theft.
Prosoft’s data encryption service covers Transparent data encryption as well as wallet management, network encryption, RADIUS, Kerberos, and SSL authentication.
We deliver innovative solutions to enable organizations encrypt sensitive application data on storage media – completely transparent to the applications – to prevent data tempering from outside of the database. That means if anybody bypasses the Database Management System and directly get access to the database files on the storage disks, they will not be able to see or retrieve the encrypted information. At the same time the data is transparently decrypted and presented to the authorized database users. Our data encryption service addresses encryption requirements associated with public and private privacy and security regulations such as PCI DSS.
We help organizations protect data from theft when file system access controls are compromised:
– Malicious user steals storage devices and reads database files directly.
– Malicious backup operator takes backup.
– Protecting data at rest (persistent data)
We have helped organizations benefit by implementing Data Encryption to ensure that sensitive data is encrypted, meets compliance, and provides functionality that streamlines encryption operations. Benefits include:

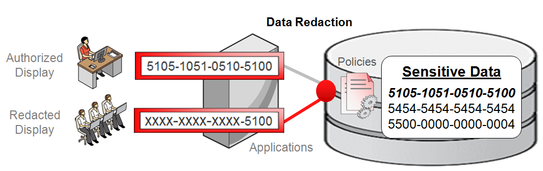
Prosoft offers innovative data redaction solutions to limit the exposure of sensitive data in production systems so that the information displayed to various application users is limited to the minimum required by them to perform their jobs.
Prosoft’s Data Redaction offering enables organizations to define masking policies for all their databases and accordingly redact sensitive data that is returned from queries issued by applications. The redaction of sensitive data is ensured to take place without altering the underlying data in the database because it is performed at runtime, that is, the moment that the user tries to view the data. Data Redaction can be applied conditionally, based on different factors such as user, application identifiers, or client IP addresses.
Organizations have derived several benefits from using Prosoft’s Data Redaction service. These benefits include:

Prosoft provides Data Masking implementation services to organizations to enable them (1) protect against the risk of exposing sensitive data to non-production users in a test environment and prevent data breaches, and (2) comply with data privacy laws and standards. Data privacy standards emphasize on protecting sensitive information in non-production environments because these environments are typically not as protected or monitored as production systems.
Data masking is ideal for virtually any situation when confidential or regulated data needs to be shared with non-production users. These users may include internal users such as application developers, or external business partners such as offshore testing companies, suppliers and customers. These non-production users need to access some of the original data, but do not need to see every column of every table, especially when the information is protected by government regulations.
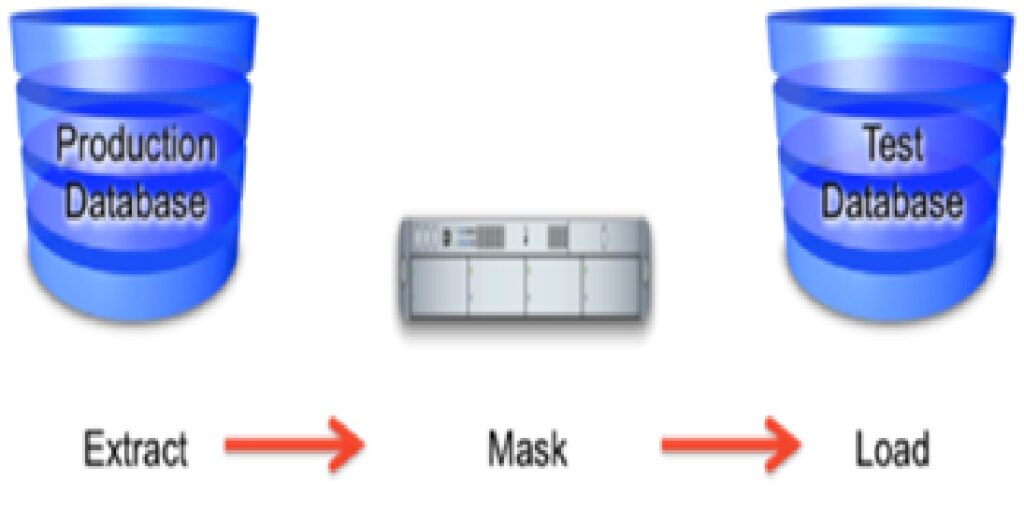
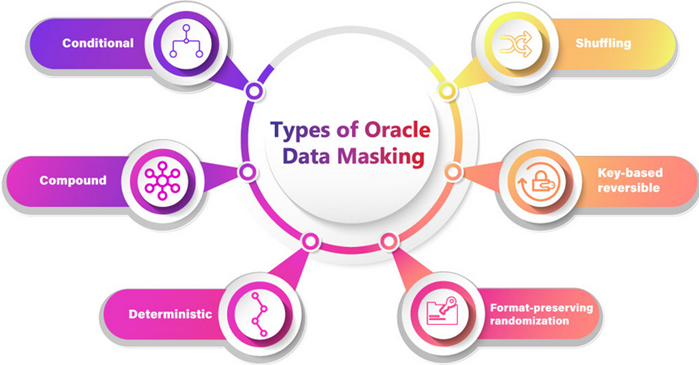
Prosoft’s data masking service helps organizations generate realistic and fully functional data with similar characteristics as the original data to replace sensitive or confidential information, such that the original sensitive data cannot be retrieved or accessed.
We have helped organizations benefit by implementing Data Masking to protect sensitive information in non-production environments to comply with regulatory requirements such as Sarbanes-Oxley, Payment Card Industry Data Security Standard (PCI DSS), Health Insurance acts as well as numerous other laws and regulations that restrict the use of actual customer data. The benefits include:

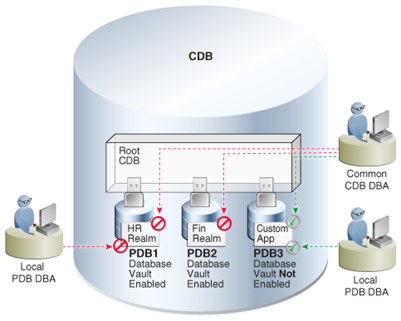
Label Security uses row level data classifications to enforce access controls restricting users to only the data they are allowed to access. It enables organizations to control their operational and storage costs by enabling data with different levels of sensitivity to co-mingle within the same database. Label Security also provides a cost-efficient way to address regulatory requirements for managing access to data on a need to know basis.
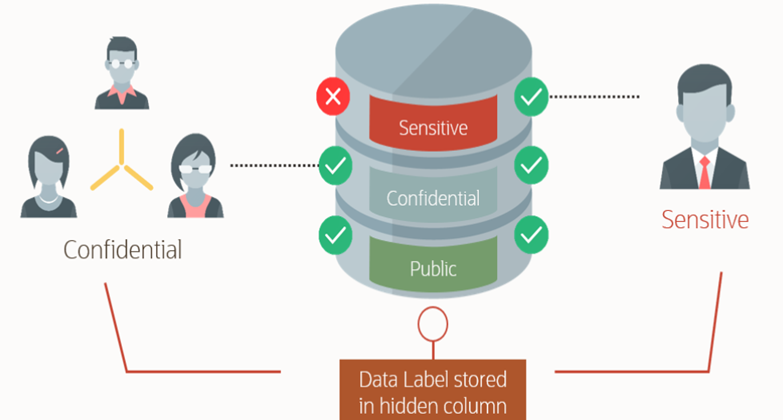
Prosoft implements Label Security solution to secure database tables at the row-level, allowing you to filter user access to row data based on privileges. The solution controls the display of individual table rows using labels that are assigned to individual table rows and application users. With this, government and business organizations can label their data using different sensitivity levels, such as top secret (TS), secret (S), confidential (C), unclassified (UC), depending on the perceived risk levels. Users are assigned different clearance levels based on their job functions and seniority. Each user is allowed to access only those data records with the sensitivity level no more than the clearance level of the user. For example, a user assigned the clearance level C can access data records with the sensitive levels C or UC only, and is not allowed to access data records with sensitivity levels greater than C, that is, TS or S.

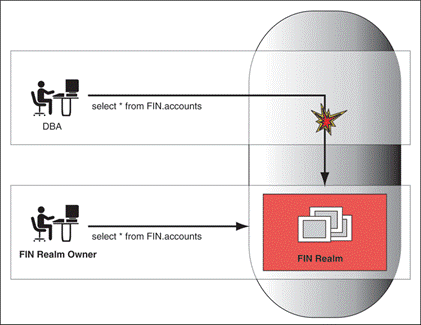
Prosoft offers advisory and implementation services for fine-grained access control to your sensitive data, including protecting data from privileged users – controls to prevent unauthorized privileged users from accessing sensitive data and to prevent unauthorized database changes.
Prosoft’s offering provides essential safeguards against common threats, including:


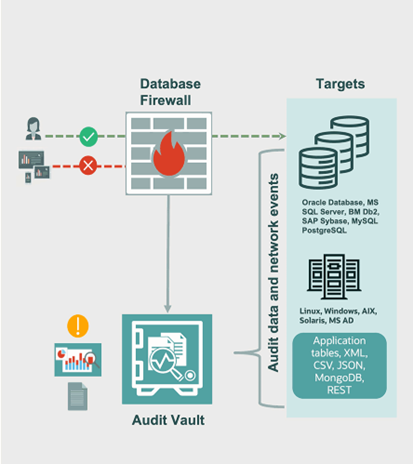
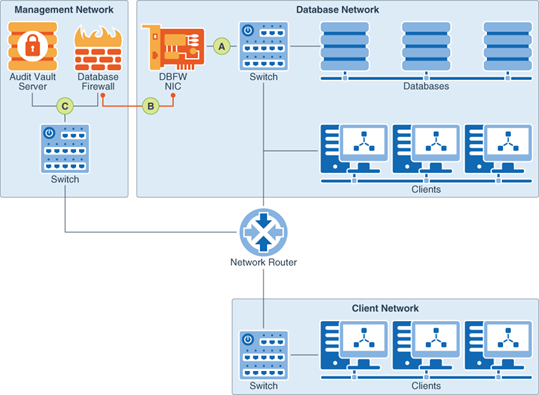
Prosoft helps organizations to implement innovative database firewall solutions that support white list, black list, and exception list based polices to monitor database traffic to detect and block threats, as well as improve compliance reporting by securely consolidating audit data from databases, operating systems, directories, and other sources. This enables perimeter security controls, providing a first line of defense around databases by monitoring in-bound SQL and blocking unauthorized SQL statements. The system examines the grammar of the SQL statements being sent to the database, analyzes their meaning, and determines the appropriate security policy to apply. It uses a sophisticated grammar analysis engine to inspect SQL statements before they reach the database and determines with high accuracy whether to allow, log, alert, substitute, or block the incoming SQL. Grammatical classification and session-factor profiling provide a powerful method for tracking database access, and enables the system to recognize changes in normal behavior, such as SQL injection attacks on applications, and block them before they reach the database.
A white list is simply the set of approved SQL statements that the firewall expects to see. A black list includes schemas, tables, users, and SQL statements that are not permitted to be sent to the database. Exception list based policies provide additional deployment flexibility that can be used to override the white list or black list policies. Policies can be enforced based upon attributes including SQL category, time of day, application, user, and IP address. The system can log queries, raise alerts, block the incoming SQL statement, or substitute it with a harmless SQL statement. This flexibility, combined with advanced SQL grammar analysis, provides organizations graceful application handling of unauthorized requests.